How to Use Security Gate Access Control Systems to Protect Your Business
Controlling access is a vital part of security. If you can successfully keep people out of your property, you can drastically reduce crime. However, there are many different ways to prevent access. Security gate access control systems are common, but there are several different ways to secure these gates.
The method that you choose can significantly affect your business. Not only are some methods more effective at securing access, but there are different costs associated with each type of security as well as different benefits.
To understand how to best use security gate access control systems at your company, it’s important to look at the options. Once you know what’s out there, you can compare the choices to your needs and determine which set up is right for you.
In addition, understanding the access control meaning and why access control matters is a significant aspect of choosing the right system. Once you can recognize the threats that are possible against your property, and the access control types that are available, you can make an informed decision for your business.
Why Access Control Matters
Maintaining security at your access gate is important. As mentioned, this is because keeping criminals and suspicious persons out of your property is crucial. It’s much more difficult to stop a criminal once they’ve already gained access to a site than if they are stopped before they can get in. Plus, criminals cause costly damage when they commit crimes, so keeping them out saves your business money and avoids hassles.
Strong access control security keeps criminals out. Different access control types work in different ways, but the basic goal remains the same: keeping unauthorized people out of a site while allowing those who are authorized to enter to do so.
The second part of that statement is an important, but sometimes overlooked part of the access control meaning. Keeping criminals out is crucial, but you want to make sure that your access control security system also does not place an unnecessary burden on authorized people. If someone is supposed to be able to get through your access gate and onto your site, you don’t want to make it incredibly difficult for them to do so.
For instance, an industrial or commercial access gate needs to be set up so that deliveries and drivers can easily get through without hassle. If it is a complicated or lengthy process to get through the access gate, this will negatively affect the timing of deliveries and shipments and hurt the efficiency of your business.
Therefore, when considering different access control types, it’s important to focus on those that are both effective at stopping unauthorized access while remaining easy-to-use for those who are authorized. By focusing on this access control meaning, a business can find much greater success.

Choosing Access Control Systems for Small Business
Preventing access to a property is an important part of any security setup. If you can keep criminals out of a location, you have a much better chance of keeping it safe. Of course, the right access control systems for business use are the ones that make it easy for staff and visitors to enter but keep unauthorized persons out.
For this job, many small businesses look to cloud-based access control systems. A cloud based access control system can be accessed through an online portal so administrators can permit or deny access to a location. These options are popular choices since they can be accessed by virtually any device with an internet connection.
Plus, since the “brains” of the system are in the cloud, not only can the system be used remotely, but there’s no need to purchase and maintain a server on site. This makes them a common choice among access control systems for small business use due to their lower cost and ease of use.
Different cloud-based systems have different features and many can integrate with other security tools installed at a business, such as surveillance cameras. Since the system operates on the cloud, updates can happen quickly and easily, and any issues can be addressed remotely in real-time.
In addition, many small businesses prefer these systems since they are scalable and new locations can be added relatively quickly.
However, while there are several advantages to cloud-based access control systems, there are certainly disadvantages too. This is especially true when they are compared to remote monitoring systems.
Key Fobs and Access Control Gates
One of the most common ways to protect gates is by using key fobs, access cards, or keys (sometimes known as an RFID gate access control system). While these tools can be convenient, there are also potential risks:
Keys, fobs, or cards can be lost, making it difficult for employees to enter.
- If these are used on commercial access control systems, losing the fob can start a complicated process where the user will need to report the loss, wait for a replacement, and even potentially deal with the hassle of finding a way to access the property until the fob or card can be replaced.
If access tools are lost or stolen, they may not be noticed for quite some time. Unauthorized visitors could use these entry methods in the meantime without anyone realizing
- Your entire gate access control plan could be in jeopardy if a fob or key card is lost and this isn’t noticed for a while. Not only could the card potentially be used at the access control gate, but there is even a chance that it could be copied.
Cards, keys, and fobs can also be copied or cloned, allowing unauthorized access
- It’s possible to copy or clone the card or fob needed to open an access control gate. If this happens, it might take a very long time for your business to notice and it may not even come to light until it’s too late.
While you may be able to give staff these tools to enter your property, it isn’t possible to give all contractors, visitors, and third parties keys or fobs. This means you’ll still need a system for these individuals as they will arrive on your site. The result is that you’ll have to maintain two different systems. This can be both costly and confusing.
- For instance, commercial access control systems often need to make it possible for visitors to enter. If the system uses cards or keys, visitors will not have these tools. Therefore, you’ll need to find a way to make it possible for them to enter without compromising security
Since there are many significant flaws associated with key fobs, cards, and keys, many organizations recognize that these forms of gate access control may not be the correct choice for their business. Access control gate protection is too important to leave to a system that has many flaws.
Security Guards & Security Gates Access Control Systems
In addition to automatic gate access control, and remote gate access control, security guards are another common way to handle access control. In these situations, guards are stationed at the entrance and they are responsible for checking IDs and allowing authorized persons into the property. There are advantages to using guards in this way:
- Security guards can check to ensure that people match their identification cards, so it’s confirmed that stolen credentials are not being used
- Guards can ask follow-up questions and confirm details with visitors to determine why they are requesting entry
However, while security guards have some benefits, there are also potential drawbacks, including:
- Guards can potentially be called away from the gates if there is another security situation elsewhere on the property. This could potentially leave the gates vulnerable
- If an organization decides to hire several guards so that the gates are never unprotected, this can get quite costly
- Security guards can potentially be overwhelmed or intimidated if a large group shows up or if individuals threaten violence
When it comes to commercial gate access control systems, the expense associated with hiring security guards can be considerable. When this is added to the reality that security guards may not be able to provide the level of security that is needed, many businesses find themselves searching for other options such as automatic gate access control or remote gate access control.
Live remote video monitoring is a powerful and cost-effective alternative to security guards.
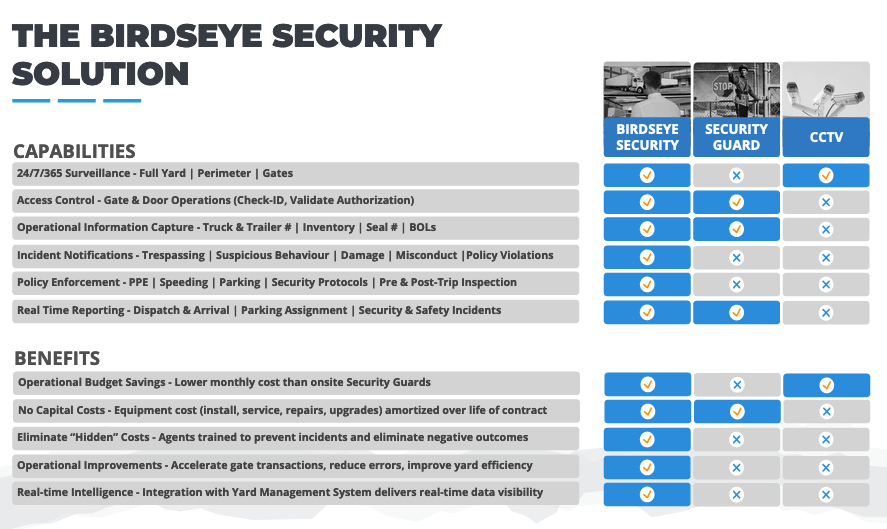
Live Remote Monitoring of Access Control Systems
Live monitoring systems involve setting up cameras, two-way speakers, and other tools to provide security. All cameras are watched by trained professional security agents. These agents can be responsible for security gate access control systems.
- Two cameras will be installed at the gate. One will be focused on the person while the other will be used to examine their identification credentials. Agents will use these views, as well as artificial intelligence (AI) to verify that the person is who they say they are
- Agents will then check the person’s identification against a list of authorized persons. If the individual is permitted to enter the property, they will be allowed to do so
- Remote security agents can ask questions and confirm information by communicating through the two-way speakers
Remote monitoring services can be set up so that agents can view the entire property from all angles. This means if anything happens anywhere on the site, they can respond right away. This enables them to secure the entire location – not just the gates – without leaving any holes.
With a live monitoring system, cameras are installed throughout a property. This lets live agents watch over the location 24/7. When someone tries to enter a door or other entry point, agents can verify if they are authorized, then either allow them to enter, deny entry, or communicate with them through two-way speakers.
When compared to cloud-based access control systems, a significant difference with remote monitoring is the lack of key cards or fobs. This improves overall security a great deal. That’s because key cards and fobs can be lost, stolen, or otherwise misplaced. The potential issue in these scenarios is that that problem won’t be noticed right away and an unauthorized person will be able to freely access your property during this time.
With remote monitoring, every person who requests access to a property or an area must be identified by the security agents that are watching the system. This provides a level of security that cannot be matched by other tools.
Another reason why live remote monitoring is a strong choice for access control systems for small business use is that monitoring services do more than just restrict access.

As mentioned, systems are often equipped with two-way speakers and other security tools. This means that they can provide more than just access control. These systems function as a comprehensive and active security tool that keeps a property safe.
For instance, in addition to stopping someone from accessing your site, remote monitoring agents can also use cameras to see what’s going on outside your property. Is someone lurking by your gate or standing outside a window with a crowbar? If they are, agents will spot them. In these instances, agents can communicate with the person directly and inform them that they are being watched. If the individual does not leave the scene, the police can be contacted directly. This is a service that cannot be offered by typical cloud-based access control systems.
In addition to handling security gate access control systems, agents can also be responsible for parking assignments and much more. This can be very useful in truck lots, automobile lots, and other locations where parking must be controlled for security or business purposes.
Remote agents can assign spots at the gate, then verify that the person parked in the correct spot. If they do not, agents can communicate with them directly to resolve the situation.
When compared with other tools (security guards, RFID access control systems, etc.) remote monitoring services can provide the comprehensive security needed to properly monitor parking assignments. If a physical guard at the front gate assigns a parking spot, they likely won’t be able to verify that the assignment was followed and they won’t have the tools needed to quickly take action to correct any issues. Of course, key fobs and access cards cannot assign spots, nor can they verify anything.
Live monitoring agents, on the other hand, perform active security. In addition to carrying out access control duties, they also watch over the entire site. If any protocols are not followed (such as someone parking in an unassigned spot), agents can react immediately to correct the issue.
For more information on remote security monitoring and how this service can strengthen security gate access control systems, please contact Birdseye Security Solutions today. We are a trusted North American leader in live video monitoring, security, and access control.




